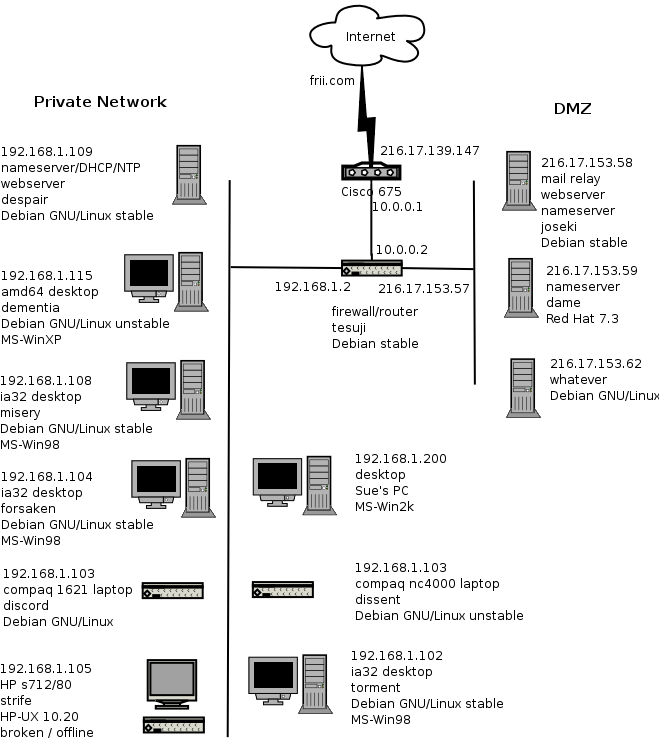

This is a standard three-legged firewall configuration with a DMZ and a private subnet. No services are provided on the firewall itself. All services accessible to the public Internet are provided in the DMZ. All general purpose desktops exist on the private subnet using RFC1918 private internet addresses. An internal server provides DHCP, DNS, NTP and other services on the internal private network. The internal network is autonomous for LAN functions. This means that WAN outages do not break the private network.
The connection policy in the DMZ is strict. Only specific incoming ports are allowed. Only specific outgoing ports are allowed. This last restriction on outgoing ports surprises some people. But these hosts are appliances dedicated to the task and do not need general outgoing access. Blocking non-allowed ports will help mitigate a security compromise on those hosts. Because the DMZ hosts are visible on the public Internet they are the target of most attacks and the most likely to suffer from a security compromise.
The connection policy in the private network is not strict. All outgoing connections are allowed, with the exception of SMTP port 25 for mail. Mail must relay through the mail relay host. This restriction prevents a possible virus infection on a MS-Win gaming machine in the private network from being an unfriendly neighbor on the Internet. With the exception of Sue's PC the only time the machines are booted into MS-Windows is for game nights. Otherwise all hosts are GNU/UNIX hosts.
This configuration has several advantages. A compromise of a host in the DMZ cannot affect hosts on the private network. The firewall host itself does not host any services. That makes it a much harder target to attack. The network view of hosts on the private network is the same as if they were behind a simple client only firewall.